The Worst Mistakes in iOS Forensics by Vladimir Katalov What can possibly go wrong with that iPhone? I’ll have a look (oh, it’s locked!), then switch it off, eject the SIM card and pass it on to the expert. Well, you’ve just made three of the five most common mistakes making subsequent unlock and extraction
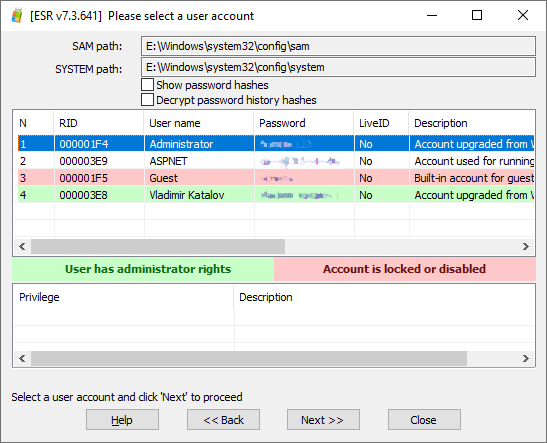
How to Unlock Windows Systems with a Bootable Flash Drive by Oleg Afonin Accessing a locked system is always a challenge. While you might be tempted to pull the plug and image the disk, you could miss a lot of valuable evidence if you do. Full-disk encryption, EFS-encrypted files and folders and everything protected with
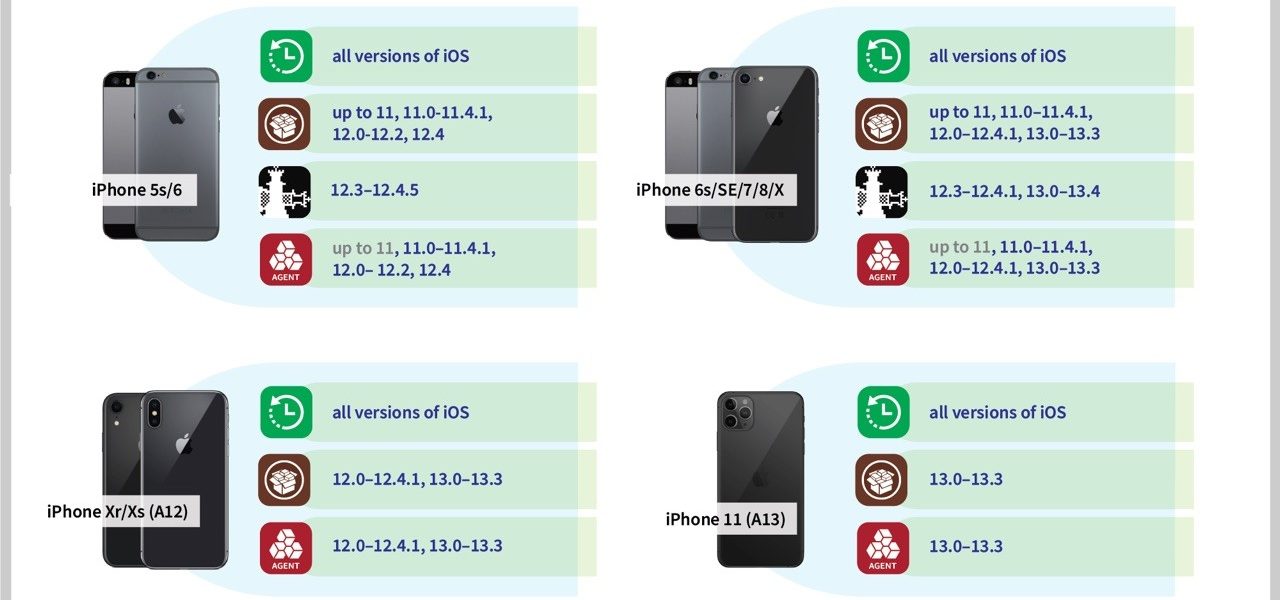
iOS acquisition methods compared: logical, full file system and iCloud by Vladimir Katalov The iPhone is one of the most popular smartphone devices. Thanks to its huge popularity, the iPhone gets a lot of attention from the forensic community. Multiple acquisition methods exist, allowing forensic users to obtain more or less information with more or
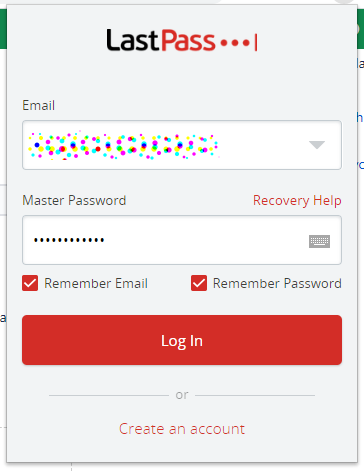
Breaking LastPass: Instant Unlock of the Password Vault by Oleg Afonin Password managers such as LastPass are designed from the ground up to withstand brute-force attacks on the password database. Using encryption and thousands of hash iterations, the protection is made to slow down access to the encrypted vault that contains all of the user’s
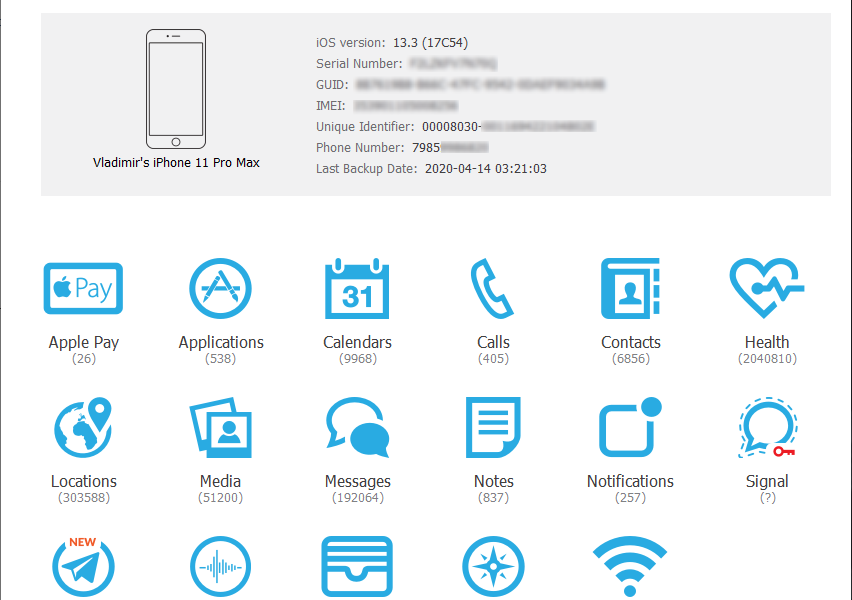
Forensic guide to iMessage, WhatsApp, Telegram, Signal and Skype data acquisition by Vladimir Katalov Instant messaging apps have become the de-facto standard of real-time, text-based communications. The acquisition of instant messaging chats and communication histories can be extremely important for an investigation. In this article, we compare the five top instant messaging apps for iOS
