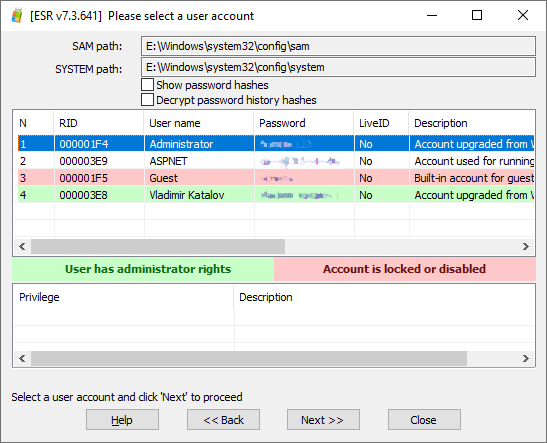
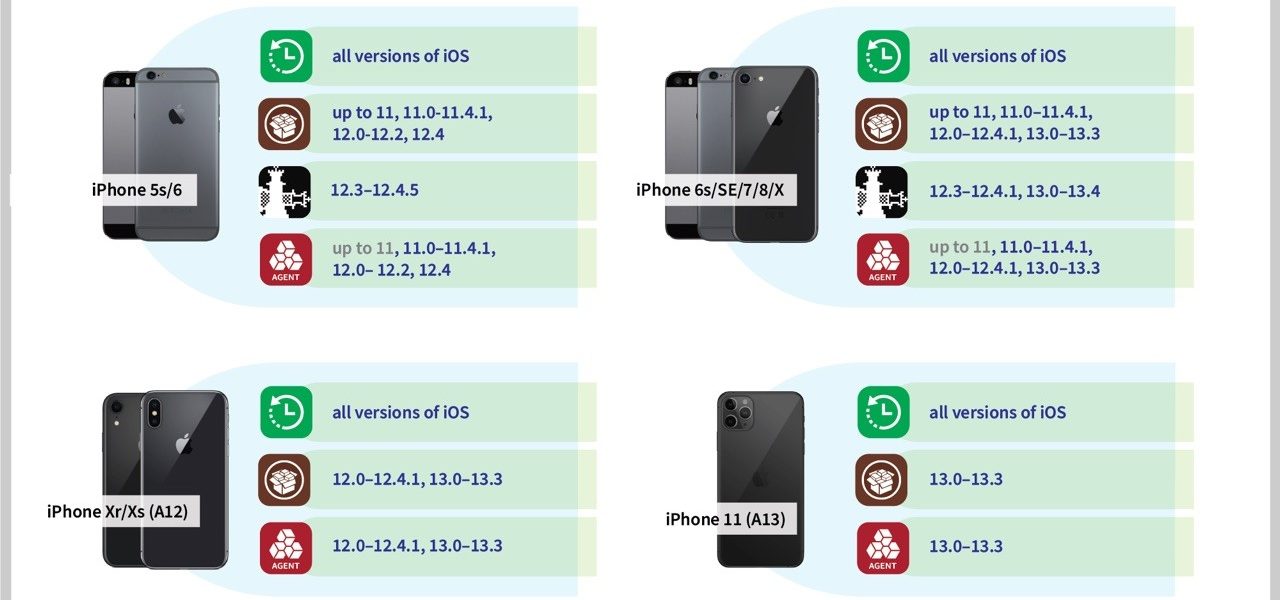
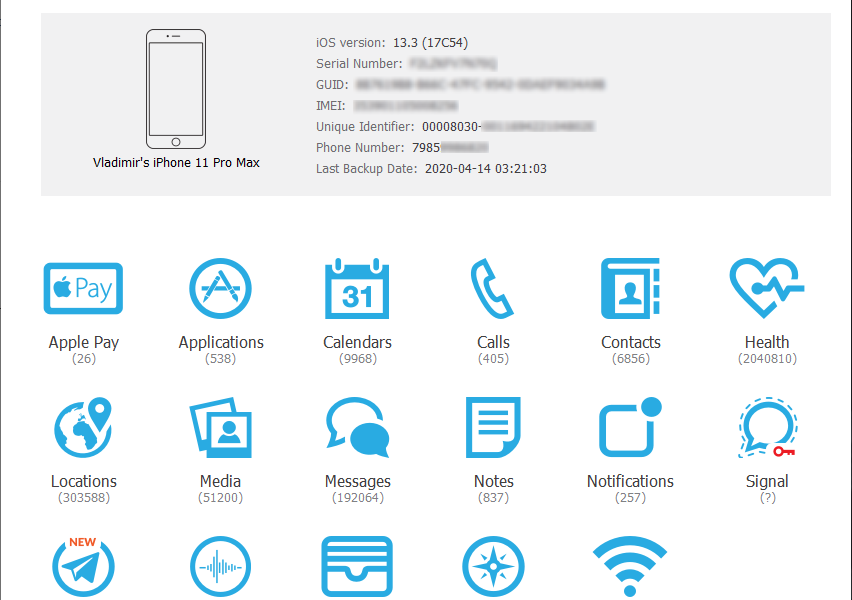
-Ritik Singh This protocol contains several rules which covers all the steps needed to comply with for completing all the process which is described below. Collection. Acquisition/imaging. Analysis Reporting. Collection:- As moving towards the collection of evidence from resources such as storage drive, hard drive, hard disk, cloud data, social media account or another digital