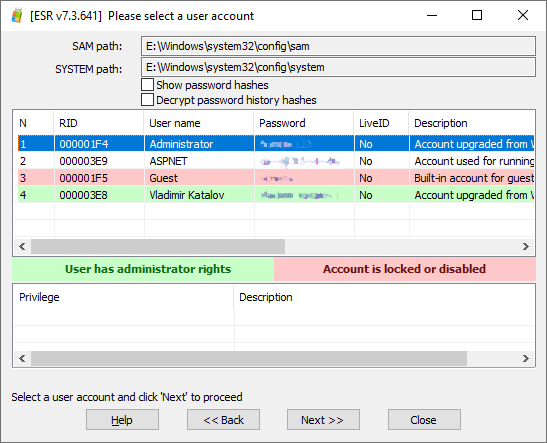
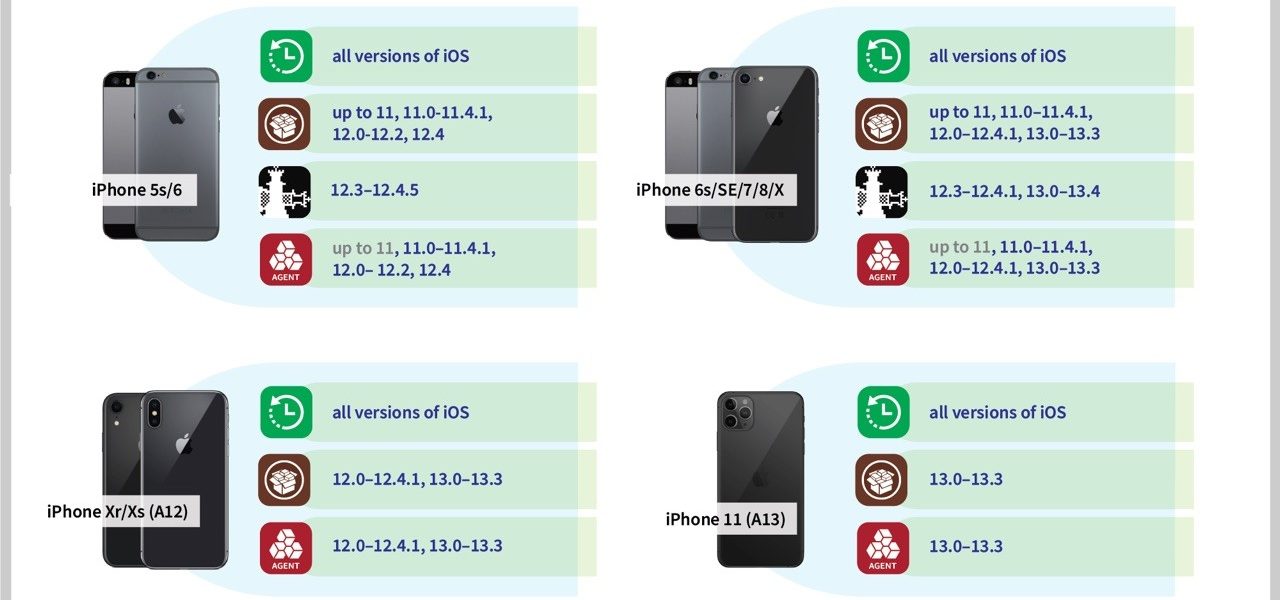
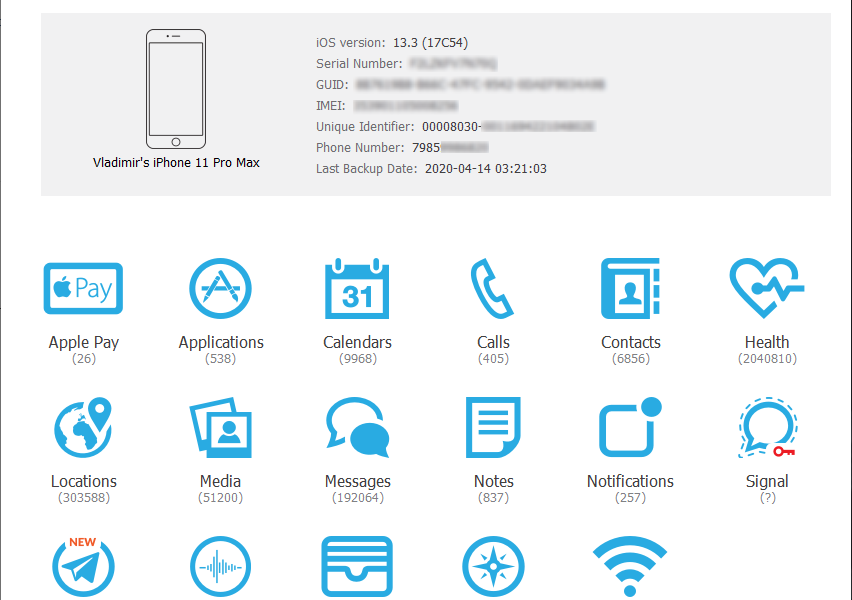
Critical National Information Infrastructure (CNII) (The views are of the author and all issues related to the contents be addressed directly to the Author) Introduction Critical National Information Infrastructure (CNII) is defined as those assets (real and virtual), systems, and functions that are vital to the nations that their incapacity or destruction would have a