Forensic guide to iMessage, WhatsApp, Telegram, Signal and Skype data acquisition
Instant messaging apps have become the de-facto standard of real-time, text-based communications. The acquisition of instant messaging chats and communication histories can be extremely important for an investigation. In this article, we compare the five top instant messaging apps for iOS in the context of their forensic analysis.
Acquisition and Extraction
Speaking of iOS, there are several methods to acquiring communications going through an instant messaging app. The MITM (man-in-the-middle) attack is practically out of the question for most modern instant messaging apps; if there are exceptions, we aren’t aware of those. Even on Android devices, a MITM attack would require installing a third-party SSL certificate, and even that may not work for some instant messengers.
The ability to obtain communication histories from the vendor is a great tool in the hands of the law enforcement. The policies of different vendors vary greatly from near-instant full disclosure to flat non-disclosure with stops in between. We’ll discuss it in detail for each of the messaging apps.
Cloud extraction may be possible from several sources, which include iCloud synchronized data (including end-to-end encrypted data), iCloud backups and stand-alone backups in iCloud Drive. It’s up to the vendor to decide where and how to store the data; more on that later.
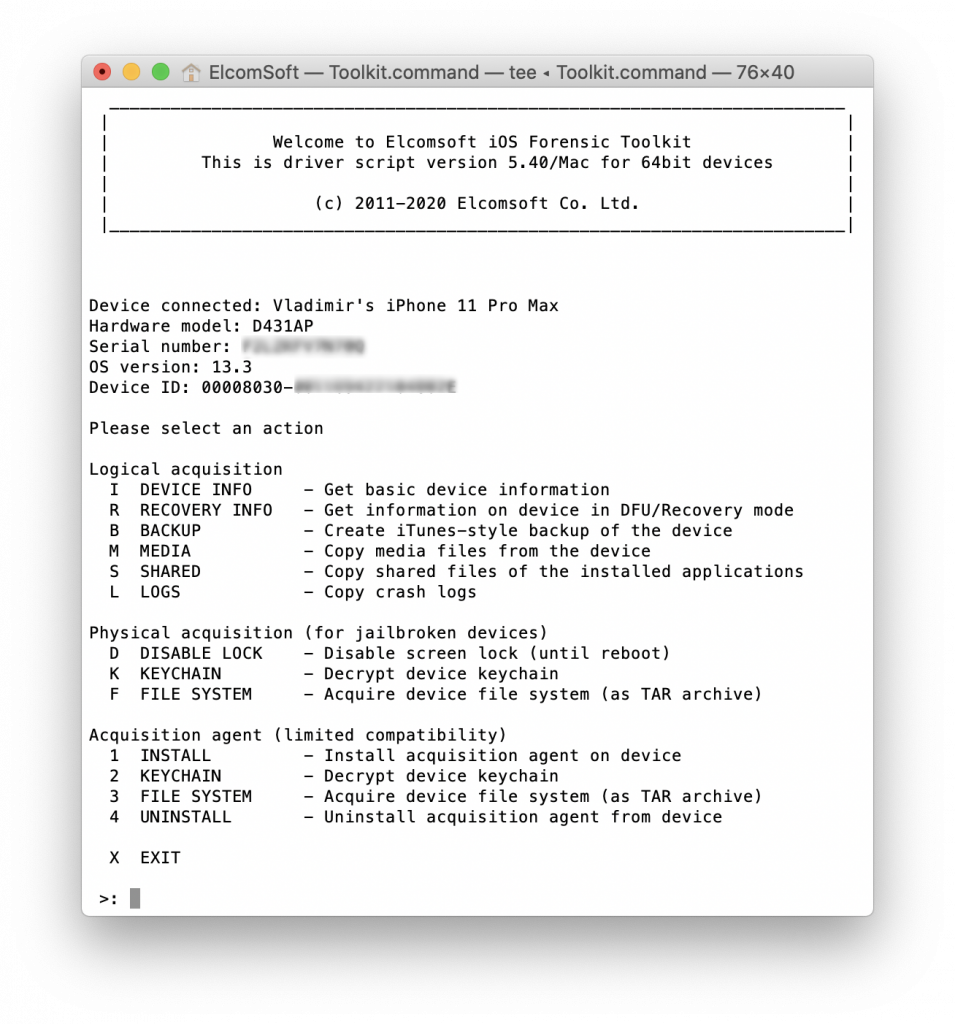
Finally, the data can be extracted from the iPhone device itself. For some messaging apps, logical extraction via iTunes-style backups is enough, while some other messengers don’t store anything in local backups. Imaging the file system (and, in some cases, decrypting the keychain) is always enough to gain full access to conversation histories.
So let us see the different extraction options available for the five top instant messaging apps for iOS.
iMessage
iMessage is preinstalled on every iPhone and iPad. Being a pre-installed app, iMessage benefits from the huge user base of the entire Apple ecosystem. Based on the information shared by Apple, iMessage is estimated to have about 1.6 billion active users worldwide, which is largely be based on the number of iPhone users. Back in 2016, the service handled some 200,000 iMessages per second.
- Legal requests: This is a bit tricky. While Apple does maintain the history of iMessage conversations on its servers, the data is protected with what Apple refers to as “end-to-end encryption”. In the end, Apple does not release iMessages when serving government requests.
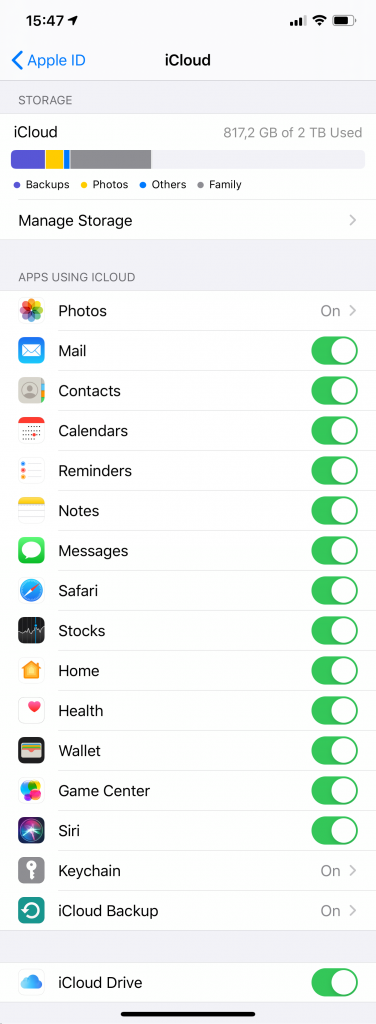
- Vendor cloud: Apple keeps a copy of iMessage conversations in iCloud. The data is encrypted with a key protected with the user’s screen lock passcode or system password. While it is possible to obtain iMessages from iCloud, one will need the complete set of authentication credentials including the user’s Apple ID and password; second authentication factor; and screen lock passcode or system password of one of the user’s devices.
- Local backups: iMessages are always available in local backups. Logical acquisition allows extracting the messages.
- iCloud backups: Apple only stores iMessages in iCloud backups if syncing (iCloud Messages) is not enabled.
- iCloud Drive: n/a.
- File system: iMessage does not feature any additional protection to the working database. Once a file system image is captured from the iPhone, extracting and analyzing iMessage conversations is straightforward.
iMessage Verdict
The acquisition of the user’s iMessage communications is possible but tricky because of the multiple ‘ifs’ and ‘buts’. iMessage conversations can be extracted from multiple sources, the exact list of which, however, depends on the user’s configuration.
Tools required: Elcomsoft iOS Forensic Toolkit (file system) or Elcomsoft Phone Breaker (iCloud, iCloud backups, iTunes backups); Elcomsoft Phone Viewer (viewing and analyzing).
Walkthrough: Messages in iCloud: How to Extract Full Content Including Media Files, Locations and Documents, iMessage Security, Encryption and Attachments.
With more than 2 billion users worldwide, WhatsApp is one of the most popular (if not the most popular) instant messengers worldwide. While WhatsApp communication is based on the Signal protocol employing end-to-end encryption, that fact alone does not make WhatsApp any more secure than other messaging apps as WhatsApp keeps a backup of its conversation histories, making them easily accessible with several acquisition techniques.
- Legal requests: WhatsApp does not store conversation histories on its servers. As a result, only pending (undelivered) messages can be obtained with a legal request.
- Vendor cloud: Facebook does not keep WhatsApp conversations on its servers, and cloud acquisition is not generally possible with one exception. Undelivered (pending) messages are still stored on the server, and can be downloaded with forensic software by authenticating as a new WhatsApp client.
- Local backups: More often than not, WhatsApp communication histories show up in both local and cloud iOS backups (there are exceptions).
- iCloud backups: Same as above. More often than not, WhatsApp conversation histories can be extracted from iCloud backups.
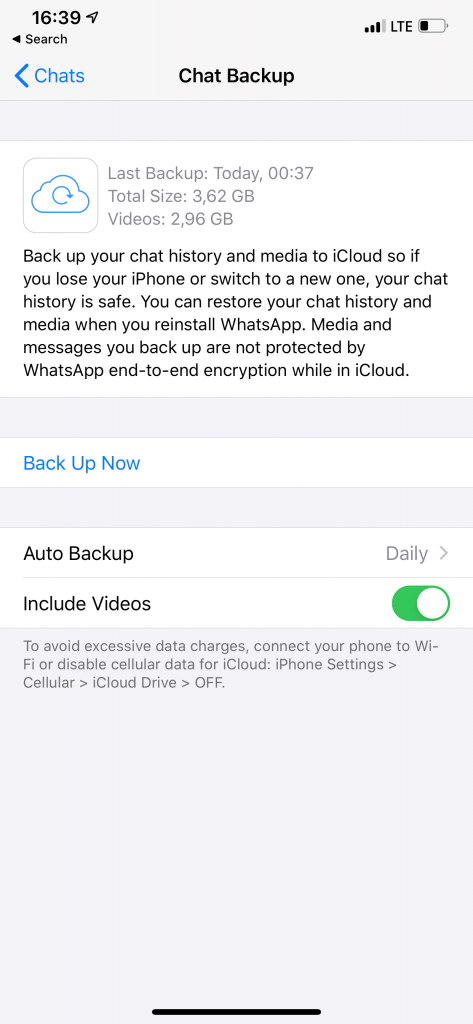
- iCloud Drive: WhatsApp has an option to save stand-alone, proprietary backups in iCloud Drive. While these backups can be easily downloaded, they are protected with end-to-end encryption. As a result, one must authenticate as a WhatsApp client in order to decrypt the backup (e.g. using Elcomsoft Explorer for WhatsApp). This requires access to the user’s registered WhatsApp number.
- File system: WhatsApp does not feature any additional protection to the working database. Once a file system image is captured from the iPhone, extracting and analyzing WhatsApp conversations is straightforward.
WhatsApp Verdict
The acquisition of the user’s WhatsApp communications is easier than average. WhatsApp conversations can be extracted from nearly every available source including local and cloud backups.
Tools required: Elcomsoft iOS Forensic Toolkit and Elcomsoft Phone Viewer; or Elcomsoft Explorer for WhatsApp.
Walkthrough: Extract and Decrypt WhatsApp Backups from iCloud.
Telegram
Telegram offers one of the most advanced cross-platform messaging experiences in the world of instant messengers. Offering apps for nearly every platform imaginable, Telegram can be used on multiple mobile devices and desktop computers. Unlike the strictly single-client WhatsApp, Telegram users can sign in on multiple devices at the same time. In 2018, Telegram reached 200 million monthly active users with nearly 300 million messages delivered daily.
Telegram uses a cloud service to deliver, store and synchronize messages. The service offers privacy conscious users the option to chat privately with the option called ‘secret chats’. Secret chats, unlike regular conversations, are never stored on Telegram servers.
- Legal requests: Telegram keeps a comprehensive history of the user’s regular (non-secret) chats on its servers. Regular and group chats can be obtained with a legal request depending on jurisdiction. Secret chats are never stored and cannot be obtained with a legal request. Telegram is notable for ignoring legal requests in some jurisdictions, which had led the service banned in several countries.
- Vendor cloud: As mentioned above, Telegram keeps the history on its own servers. By authenticating as a user, one can retrieve those communications (except secret chats) from Telegram servers.
- Local backups: Telegram does not store conversations in local backups. Instead, conversation histories are synchronized using Telegram’s own cloud service.
- iCloud backups: Same as above. Telegram does not store conversation histories in iCloud backups.
- iCloud Drive: There are no stand-alone backups in iCloud Drive.
- File system: Telegram does not feature any additional protection to the working database. Once a file system image is captured from the iPhone, extracting and analyzing Telegram conversations including secret chats and attachments is trivial.
Telegram Verdict
We consider the complexity of Telegram acquisition to be about average. Telegram conversations (including secret chats) can be extracted from iOS file system images. Regular chats can be obtained with a legal request from Telegram, although the company can be picky about those at least in some jurisdictions.
Tools required: Elcomsoft iOS Forensic Toolkit (to extract the file system); Elcomsoft Phone Viewer (to analyze the Telegram database).
Walkthrough: How To Extract Telegram Secret Chats from the iPhone
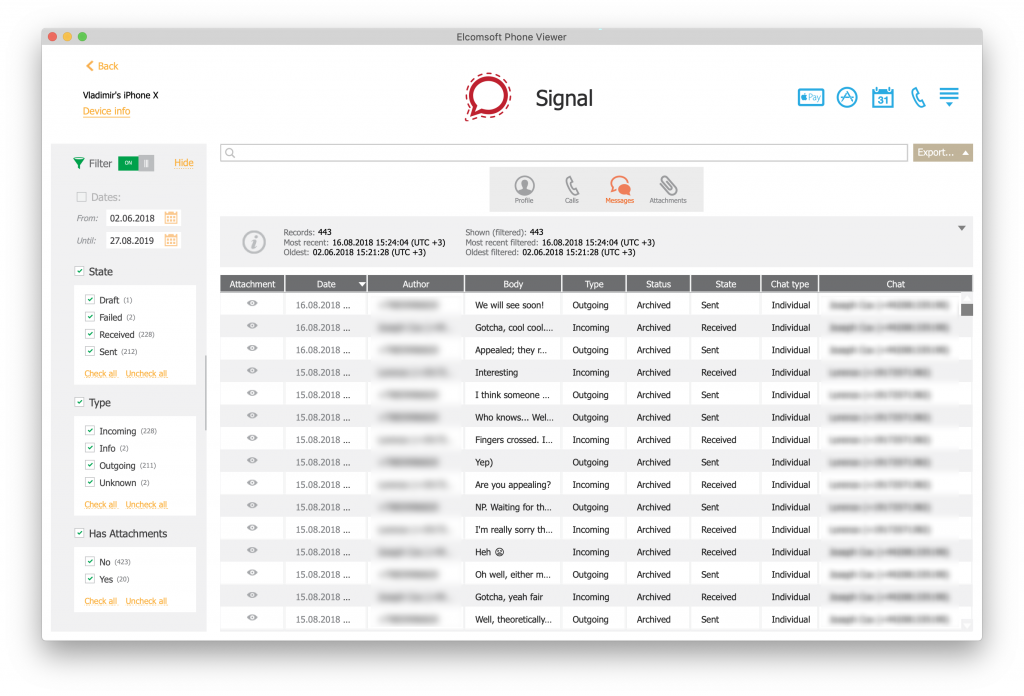
Signal
Judging by sheer numbers, Signal does not appear to be popular or widespread. However, this instant messenger was developed and marketed as the tool offering the ultimate privacy and security of communications. Barely reaching half a million users, Signal had already become the de-facto communication choice by those who have something to hide.
Signal implements a highly secure communication protocol employing end-to-end encryption. Unlike WhatsApp, which is based on the same protocol, Signal’s implementation is a lot more secure. Signal encrypts messages in transit and does not store conversation histories on its servers. Moreover, Signal encrypts its working databases, making acquisition difficult even if one has access to the physical device.
- Legal requests: Signal does not keep communication histories its servers. Since there is nothing to request, Signal conversations cannot be obtained with legal requests.
- Vendor cloud: Signal does not keep conversations on its servers. Cloud acquisition is not possible.
- Local backups: Signal does not store conversations in local (iTunes) backups.
- iCloud backups: Same as above. Signal does not store conversation histories in iCloud backups.
- iCloud Drive: No stand-alone backups in iCloud Drive.
- File system: Signal database is encrypted. The encryption key is stored in the keychain with the highest protection class. Extracting and decrypting the keychain (e.g. with Elcomsoft iOS Forensic Toolkit) is required in order to decrypt the Signal database.
Signal Verdict
Signal is one of the more difficult messengers to acquire. The only way to extract Signal conversations requires extracting the file system images and decrypting the keychain. Logical, cloud and legal requests are useless.
Tools required: Elcomsoft iOS Forensic Toolkit (to extract the file system and decrypt the keychain); Elcomsoft Phone Viewer (to decrypt and analyze the Signal database).
Walkthrough: How to Extract and Decrypt Signal Conversation History from the iPhone
Skype
Skype is one of the oldest instant messaging apps around. The Microsoft owned instant messaging service has apps for most popular platforms. In March 2020, Skype is used by 100 million people on a monthly basis. Some 40 million people use it daily. Microsoft retains Skype conversation histories on its servers. Offering no ‘private’ or ‘secret’ communication options and readily cooperating with local governments, Microsoft delivers the most law enforcement friendly service of them all.
- Legal requests: Microsoft keeps a comprehensive history of the user’s Skype conversations on its servers. Microsoft readily cooperates with the law enforcement, allowing to obtain Skype communications via legal requests.
- Vendor cloud: Microsoft keeps Skype conversations on its servers. Experts can download Skype histories by signing in to the user’s Microsoft Account.
- Local backups: Skype no longer keeps conversations in local backups. Instead, conversation histories are synchronized via the user’s Microsoft Account.
- iCloud backups: Same as above. Microsoft does not store conversation histories in iCloud backups.
- iCloud Drive: There are no stand-alone Skype backups in iCloud Drive.
- File system: Skype does not feature any additional protection to the working database. Once a file system image is captured from the iPhone, extracting and analyzing Skype conversations is a breeze.
Skype Verdict
We consider the complexity of Skype acquisition to be about average. Skype does not have ‘secret’ chats, nor does it use end-to-end encryption of its database. Skype conversations can be extracted from iOS file system images. Microsoft readily cooperates with the law enforcement, allowing to obtain Skype communications via legal requests. In addition, Skype communications can be extracted from the cloud by authenticating as a user.
Tools required: Elcomsoft Phone Breaker (Microsoft Account); Elcomsoft Phone Viewer (to view the data).
Walkthrough: Extracting Skype Histories and Deleted Files Metadata from Microsoft Account
Conclusion
There are many more instant messengers around than we can deal in a single article. Line, Viber, QQ, WeChat, Facebook Messenger and many more other messaging apps are available for various platforms. We’ll continue our research, gradually adding support for additional communication tools.
Source : https://blog.elcomsoft.com/2020/04/forensic-guide-to-imessage-whatsapp-telegram-signal-and-skype-data-acquisition/
Reposted with consent from the Author