This post is reproduced as it is from from https://blog.elcomsoft.com/2017/09/new-security-measures-in-ios-11-and-their-forensic-implications/
Apple is about to launch its next-generation iOS in just a few days. Researching developer betas, we discovered that iOS 11 implements a number of new security measures. The purpose of these measures is better protecting the privacy of Apple customers and once again increasing security of device data. While some measures (such as the new S.O.S. sequence) are widely advertised, some other security improvements went unnoticed by the public. Let us have a look at the changes and any forensic implications they have.
Establishing Trust with a PC Now Requires a Passcode
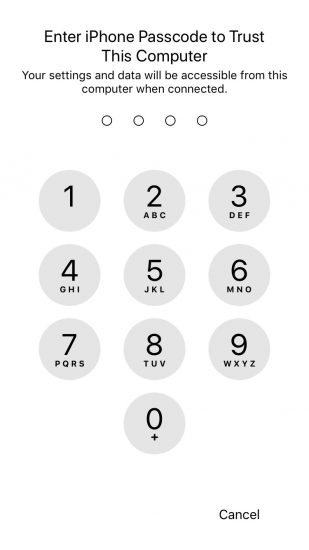
For the mobile forensic specialist, one of the most compelling changes in iOS 11 is the new way to establish trust relationship between the iOS device and the computer. In previous versions of the system (which includes iOS 8.x through iOS 10.x), establishing trusted relationship only required confirming the “Trust this computer?” prompt on the device screen. Notably, one still had to unlock the device in order to access the prompt; however, fingerprint unlock would work perfectly for this purpose. iOS 11 modifies this behaviour by requiring an additional second step after the initial “Trust this computer?” prompt has been confirmed. During the second step, the device will ask to enter the passcode in order to complete pairing. This in turn requires forensic experts to know the passcode; Touch ID alone can no longer be used to unlock the device and perform logical acquisition.
The trust relationship and why it is needed
Establishing a trust relationship between an iOS device and the PC is required in order to perform logical acquisition. Without pairing the device to the PC, experts will be unable to make a local backup of the device. Considering current situation with iOS 11 jailbreak, physical acquisition is not (yet) an option, so logical (and cloud) acquisition is currently the only way to go.
Before: iOS 8 through iOS 10
In order to establish a trusted relationship, users would perform the following sequence:
- Connect the iOS device to the computer. iTunes must be installed and launched at least once on that computer in order for the pairing to work.
- Unlock the device with Touch ID or by entering the passcode (if enabled).
- Tap Trust on the “Trust This Computer?” prompt on the device.
- In iTunes, tap Continue. The trust relationship between the iOS device and the computer is now established.
Now: iOS 11
iOS 11 introduces an extra step when establishing trusted relationship. The new pairing sequence:
- Connect the iOS device to the computer. iTunes must be installed and launched at least once on that computer in order for the pairing to work.
- Unlock the device with Touch ID or by entering the passcode (if enabled).
- Tap Trust on the “Trust This Computer?” prompt on the device.
- In iTunes, tap Continue.
- If the iOS device has a passcode, it will now prompt to enter the passcode. The trust relationship between the iOS device and the computer will be only established after you enter the correct passcode.
Forensic implications
Prior to iOS 11, it was possible to perform logical acquisition of an iOS device by unlocking the device with Touch ID. The new pairing procedure requires the use of device passcode in order to establish trust between the device and the computer, thus making logical acquisition possible only if you know the passcode.
This change is very important from the legal standpoint. While in certain cases the user may be compelled to unlock their device using their fingerprint, obtaining the passcode from the user may be challenging and, in many jurisdictions, not legally possible.
Recent cases
In particular, Apple protects their customers’ data in cases of mass device seizures with dubious warrants like the one mentioned in this Forbes article. If the user owns a device running iOS 11, forcing a fingerprint unlock will no longer allow investigators to gain access to information other than what can be manually accessed on device screen.
The S.O.S. Mode
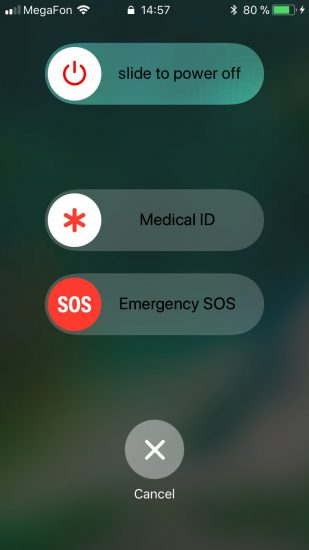
In iOS 11, Apple has added an new emergency feature designed to give users an intuitive way to call emergency by simply pressing the Power button five times in rapid succession. As it turns out, this SOS mode not only allows quickly calling an emergency number, but also disables Touch ID.
Once the Power button (Sleep/Wake) is pressed five times in rapid succession, the iPhone displays a menu presenting various options including an option to cancel. Regardless of the option chosen (including the Cancel button), iOS will temporarily disable Touch ID and require the user to enter a passcode in order to unlock the device.
Forensic implications
This feature can be used to discretely disable Touch ID in situations where the user might be compelled to unlock their phone with a fingerprint. Once Touch ID is disabled, there is no other way to unlock the device but using the passcode or making use of an existing pairing record.
There is no way for to tell that Touch ID has been disabled by using the SOS feature. Once the sequence is completed and the user cancels the menu, the iPhone prompts for a passcode in the same manner it uses after Touch ID naturally times out.
Using existing pairing records to unlock
Even if the iPhone has been locked using the emergency feature, it may still be unlocked for logical acquisition using a valid pairing record extracted from the user’s computer. It is essential that the iPhone in question remains powered on and is not allowed to shut down or reboot before the unlock is attempted.
If the user has engaged the SOS mode, or if Touch ID has expired according to Apple’s rules, a valid pairing record will still allow you to get in and to produce a backup. You will need to use the last version of Elcomsoft iOS Forensic Toolkit for that. In order to unlock the device with pairing record, launch iOS Forensic Toolkit and choose option “B” for “Backup”. You will be prompted for a file containing the lockdown (pairing) record.
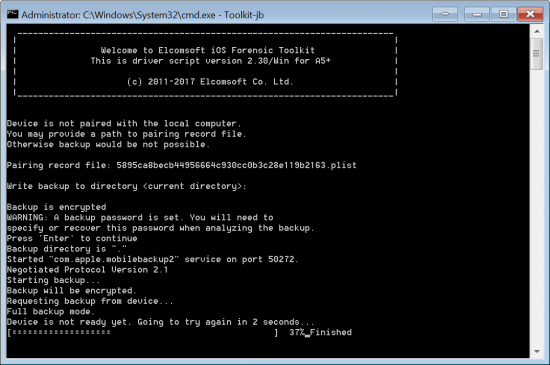
Lockdown records are saved in the following locations:
Windows Vista, 7, 8, 8.1, Windows 10:
%ProgramData%\Apple\Lockdown
Windows XP:
%AllUsersProfile%\Application Data\Apple\Lockdown
macOS:
/var/db/lockdown
While not directly related to iOS 11, it is important to note that macOS 10.2 and newer implement access control to restrict access to pairing records. This can be fixed by running the following command in console:
sudo chmod 755 /var/db/lockdown
There is also another issue with pairing records, and this time it is directly related to iOS 11. This issue apples to iOS Forensic Toolkit in macOS and Windows. Even as the connected device is already paired with the current system, EIFT does not recognize the device and asks for a pairing record. A workaround is simple; just enter the path to the pairing record when requested. In Windows, do not forget using the quotes:
“C:\Users\All Users\Application Data\Apple\Lockdown\{ID}.plist”
/var/db/lockdown/{ID}.plistWe are going to address the second issue in EIFT 2.31 that will be released shortly. As for the lockdown folder access problem, we decided to address it in the user’s manual instead of changing permissions automatically due to potential security drawbacks.
Once again, for successfully unlocking the device with a pairing record it is essential that the iPhone in question remains powered on and is not allowed to shut down or reboot before the unlock is attempted.
More information about extracting and using pairing records in this article:
Using Pairing Records in iOS 11
One relative weakness related to pairing records is carried over from previous versions of iOS. Namely, if the user changes their passcode, all existing pairing records are not revoked. As a result, all existing pairing records remain valid and are not automatically invalidated after the user adds, removes or changes device passcode, adds or removes fingerprints. Moreover, in iOS 11, pairing records still do not have a set expiry date.
Forensic implications
Your ability to unlock devices with pairing records extracted from the user’s computer(s) remains unaffected even if the user adds, removes or changes authentication methods (passcode, fingerprint). However, in order to successfully unlock the device with a pairing record it is still essential that the iPhone in question remains powered on and is not allowed to shut down or reboot before the unlock is attempted.
Our take
This is one of the few obvious weaknesses still remaining in the iOS 11 security system. If Apple decides to automatically invalidate already issued pairing records on changing authentication methods (fingerprint/passcode or even just the passcode), or simply makes cryptographic keys in pairing records passcode-dependent, a major acquisition possibility may be locked.
At this time, pairing records do not have a set expiry date. They survive through reboots (providing that the phone has been unlocked with a passcode at least once after a reboot) and changes of authentication methods. It is known that Apple has full control over lifespan of the pairing records. The company may or may not change existing behaviour in the future.
Notifications No Longer Stored in Backups
In March, 2017, we discovered a way to extract undismissed notifications from iOS backups. Notifications are pushed by pretty much every app of forensic significance. Email clients and instant messengers, Uber and taxi apps, booking and travel services, online shopping and delivery services, social networks and banking apps are just a few things to mention. Unless read or dismissed, these notifications were stored in local and cloud backups.
More importantly, these notifications were kept in the backups forever. The user only has access to notifications from the last 7 days. Older notifications automatically disappear from the device notifications shade. For some reason these old notifications were still kept on the device; they were backed up and restored using both local and cloud backups.
This is no longer the case. Notifications are no longer part of any backups, local or iCloud. With no iOS 11 jailbreak (yet), we have no way to verify whether notifications older than 7 days are still stored on the device or not.
Forensic implications
You now have one less piece of information available via logical or cloud-based acquisition process. Access to undismissed notifications with ElcomSoft tools lasted for less than 7 months.
A Word on Two-Factor Authentication
Two-factor authentication has been around for a while. First introduced in iOS 9 as a successor to the old and insecure Two-Step Verification, the new 2FA method has proved to offer a reasonable balance between security and convenience. In iOS 11, Apple starts pushing two-factor authentication much harder, up to the point of displaying a prominent pending notification dot over the Settings icon. By opening Settings, the user will see a pending notification reminding to enable two-factor authentication.
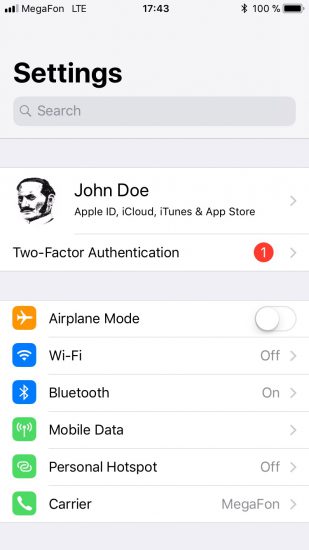

Notably, two-factor authentication is not yet universally available. The up to date list of regions where 2FA is already available at Apple’s Web site: https://support.apple.com/en-us/HT205075
ElcomSoft products support most Two-Factor Authentication methods including codes pushed to trusted devices as well as offline codes generated on trusted devices. We don’t currently support codes delivered as text messages.
iCloud tokens can still be used to bypass two-factor authentication in iOS 11. By extracting an authentication token from the user’s i-Device, Mac or PC (the latter must have iCloud for Windows installed), experts can sign in to the user’s iCloud account without knowing the user’s Apple ID or password and without having to go through the second authentication step. Do note that iCloud tokens expire. More on the expiration of iCloud tokens as well as additional details on how to extract them in our blog.
One more thing. If Two-Factor Authentication is active on the user’s account, gaining access to the user’s iCloud Keychain is somewhat easier as one only needs to have the user’s i-Device and does not need an iCloud Security Code.
Conclusion
For now, this was everything we wanted to share about the upcoming features of iOS 11. There are many more low-level and invisible changes to both the operating system and iCloud. There are changes in communication protocols, data formats and encryption. We kept an eye on the situation through all developer betas, and have already implemented support for most of them. An updated version of Elcomsoft Phone Breaker is just around the corner with support for iOS 11 local and cloud backups, the ability to download media, files, synced data and keychain produced by devices running the new OS. We are also updating Elcomsoft Phone Viewer to allow exploring local and cloud iOS 11 backups. Stay tuned for further announcements!
We take no credit for this post as it is from https://blog.elcomsoft.com .Posted it as it a very good for Forensic investigators







